Base64 attacks are becoming more and more common these days. They involve exploiting a PHP vulnerability on a website and injecting malicious, base64-obfuscated code. The main targets of such attacks are poorly coded plugins that feature security holes.
The encoded code is decoded when the infected .php file is loaded and the actual attack is carried out. A popular attack is to forward a website to another page, which grants the attacker an affiliate bonus.
Here is an example of what a base64 hack looks like in a .php file:
eval(base64_decode(“dGhpcyBpcyBhIHRlc3Q=”)); – this code will output “this is a test” when decoded. A regular base64 code snippet will be significantly longer.
On our web hosting platform, there are several ways to deal with such hacks:
Restore a backup
With our cloud hosting accounts, we offer multiple daily backups, so anyone can easily revert to a previous version of a website with just a click. And we keep backups for up to 30 days.
Here is how to choose the correct backup:
– Log into the Hepsia Control Panel and navigate to the File Manager section;
– Head to the folder pertaining to the hacked website;
– Sort the files by modified date;
This way, anyone can see when the files were last updated. When there are multiple .php files that were updated 10 days ago, simply load an earlier backup with clean versions of those files.
If there are problems restoring a backup, our support team reps will be happy to assist.
Clean the files manually
To clean the files by hand, simply download them to a computer and clean them using a text editor. The Windows/OSX-compatibleSublimeText or the Windows-compatible Notepad++, both of which are available for free, will do a great job.
Once the files are downloaded, load them in the text editor and search for any base64 code. To see if there is any base64 code on the website, use the following search term:
eval(base64_decode.
Once you discover an instance, copy the actual code snippet and search again. Simply replace the code with an empty space to get rid of it. If there are still any other base64 instances, repeat the procedure until non are left.
Regular expressions can also be used to target base64 code on the website. Again, simply replace the regex matches with an empty space to clear them from the pages.
Here is a sample regex search term: /eval\(base64_decode\((.*)\)\);/i
Keep in mind that this type of search with target all base64 instances. This means that if any plugin or element of the site is using base64 encoding as well, it will also be removed.
Clean the files over SSH
When using terminal access, all infected files can be cleaned with just a few commands over SSH. If SSH access is not enabled for the account, it can be done with a request in theUpgrades section of the Hepsia Control Panel.
The first thing that needs to be done is to get a sample of the infected base64 code. Use this as a reference for cleaning all infected files.
See which files are infected by using the following command:
$ find . -type f | xargs grep “dGhpcyBpcyBhIHRlc3Q=”
This command will search for all files in the current folder that contain the following string:
“dGhpcyBpcyBhIHRlc3Q=”.
Here is how the output of that command will look like:
./themes/default/single.php:<?php eval(base64_decode(“dGhpcyBpcyBhIHRlc3Q=));
./themes/default/search.php:<?php eval(base64_decode(“dGhpcyBpcyBhIHRlc3Q=”));
…
This will list all the infected files in the current folder and its subfolders. Once the list is ready, it’s time to eliminate the code.
We’ll use the sed program and our function will look like this:
find . -name “*.php” -print | xargs sed -i ‘s@eval(base64_decode(“dGhpcyBpcyBhIHRlc3Q=”));@@g’
Use the search function one more time to make sure that all the files are now clean. If the search returns no results, the website has been cleaned.
Preventing base64 attacks
As we’ve noted, a base64 hack will target a vulnerability in the code. So the best course of action is to always keep apps and plugins updated to the latest versions available. A good rule of thumb is to only download plugins that are actually needed. If a plugin is not used anymore – remove it from the application.
Also, when downloading new plugins, always keep track of the number of downloads and the update dates. If the last update is more than one year old, the plugin in question may be susceptible to an attack.
 Felicidades! Starting from today, you and your customers can register .MX ‘nombres de dominio’ and become a part of the large online Mexican family.
Felicidades! Starting from today, you and your customers can register .MX ‘nombres de dominio’ and become a part of the large online Mexican family.

 Since the new data center in Finland was added to our platform, the number of websites hosted on our shared hosting servers there has been growing steadily because of the favourable conditions and the secure image of the facility.
Since the new data center in Finland was added to our platform, the number of websites hosted on our shared hosting servers there has been growing steadily because of the favourable conditions and the secure image of the facility.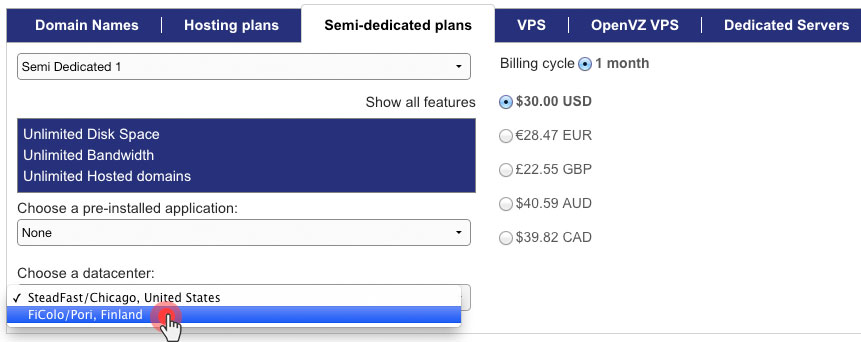
 The geographical expansion of our server network continues with the addition of semi-dedicated servers to the data centers in the UK and in Bulgaria.
The geographical expansion of our server network continues with the addition of semi-dedicated servers to the data centers in the UK and in Bulgaria.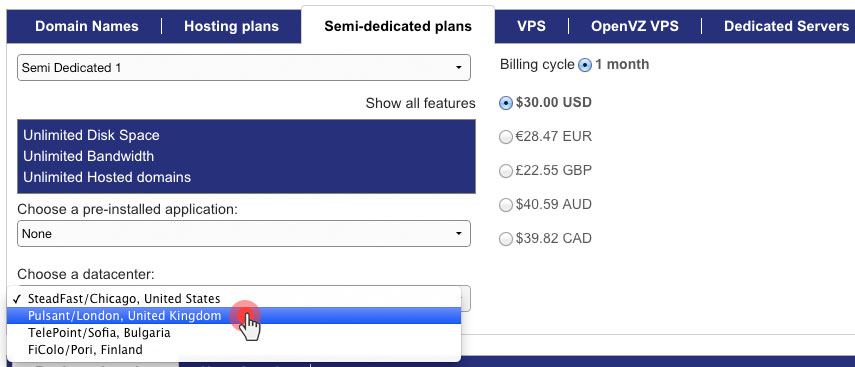
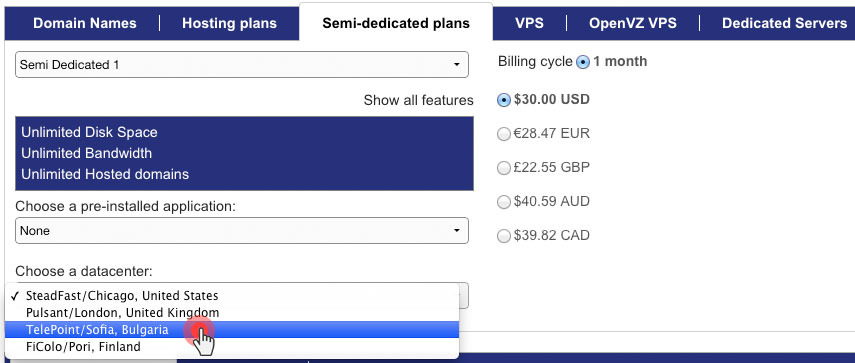
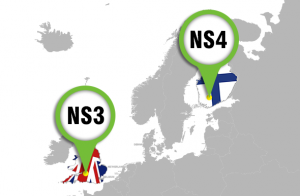
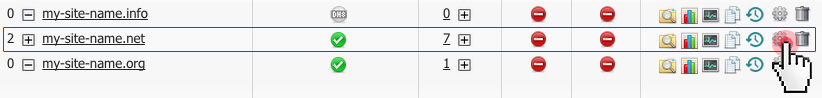
 Not long ago, we enabled the ModSecurity anti-hack firewall on all our servers to shield your hosting account from malicious online activity around the clock.
Not long ago, we enabled the ModSecurity anti-hack firewall on all our servers to shield your hosting account from malicious online activity around the clock.